Overview
Review Areas
Timeline
News
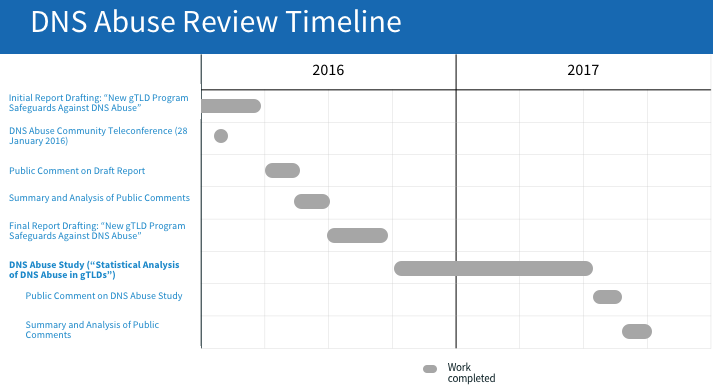
- 13 October 2017 – Staff Report Published on Public Comments Received on the Statistical Analysis of DNS Abuse in gTLDs (SADAG) Study [PDF, 503 KB]
- 13 September 2017 – Webinar recordings: Two community webinars were held with researchers from SIDN Labs and the Delft University of Technology to review the methodology and findings of the Statistical Analysis of DNS Abuse in gTLDs (SADAG) Final Report, as well as to answer questions from webinar participants.
- Webinar Slides [PDF, 2.11 MB]
- 14:00 UTC
- 04:00 UTC
- 9 August 2017 – Statistical Analysis of DNS Abuse in gTLDs (SADAG) Published for Public Comment
- 2 August 2016 – Request for Proposal for DNS Abuse Study Published
- 18 July 2016 – Revised Report on DNS Abuse and New gTLD Program Safeguards Now Available
- 17 June 2016 – Public Comment Summary Published for New gTLD Program Safeguards to Mitigate DNS Abuse Draft Report
- 15 March 2016 – Draft Report on New gTLD Program Safeguards Against DNS Abuse Available for Public Comment
Overview
The DNS Abuse Review aims to aid the work of the Competition, Consumer Choice and Consumer Trust Review Team (CCTRT) and will:
- Provide an overview of the state of Domain Name System (DNS) abuse during the first three full years (2014 – 2016) of the New gTLD Program
- Compare rates of abuse in new and legacy gTLDs
- Provide options for measuring the effectiveness of the safeguards to mitigate malicious conduct in the DNS
Review Areas
DNS Abuse Study ("Statistical Analysis of DNS Abuse in gTLDs")
The CCTRT requested a study that would measure and compare rates of common forms of DNS abuse, such as phishing, spam, and malware distribution. Following the public issuance of a Request for Proposal (RFP) in August 2016 and interviewing a number of qualified candidates based on their submissions to the RFP process, SIDN Labs was selected to carry out the study given its experience in DNS abuse measurement and analysis.
The report was published on 9 August 2017.
New gTLD Program Safeguards to Mitigate DNS Abuse Report
Ahead of the launch of the New gTLD Program, ICANN solicited advice from stakeholders to a) examine the potential for increases in abusive, malicious, and criminal activity in an expanded DNS and b) make recommendations to pre-emptively mitigate those activities through a number of safeguards. Read the original report.
Areas of potential abuse were identified by experts in a diverse array of groups, including the Anti-Phishing Working Group (APWG), the Registry Internet Safety Group (RISG), the Security and Stability Advisory Committee (SSAC), Computer Emergency Response Teams (CERTs) and members from the banking, financial and Internet security communities. After extensive consultations, the below recommendations were made to address each issue area:
Question |
Recommendation(s) |
|---|---|
How do we ensure that bad actors do not run registries? |
Vet registry operators through background checks to ensure no potential registry operator has been party to criminal, malicious, and/or bad faith behavior. |
How do we ensure integrity and utility of registry information? |
Require Domain Name System Security Extension (DNSSEC) deployment on the part of all new registries to minimize the potential for spoofed DNS records. |
How do we ensure more focused efforts on combating identified abuse? |
Require "Thick" Whois records to encourage availability and completeness of Whois data. |
How do we provide an enhanced control framework for TLDs with intrinsic potential for malicious conduct? |
Create a high security zone verification program to establish a set of criteria to assure trust in TLDs with higher risk of targeting by malicious actors—e.g. banking and pharmaceutical TLDs—through enhanced operational and security controls. |
The DNS Abuse review will focus on analyzing the implementation and effectiveness of these safeguards in mitigating DNS abuse in new gTLDs, which will serve as an input to the work of the Competition, Consumer Choice, and Consumer Trust Review Team.
Timeline
Updated 12 February 2018
News Archive
- 28 January 2016 – Online discussion on DNS abuse conducted. Download slides [PDF, 278 KB].
- 28 January 2016 – Discussion recordings: Two discussions were held to help ICANN staff formulate a definition of DNS abuse, brainstorm methods for measuring abuse, and gather qualitative, experiential input on whether safeguards to mitigate DNS abuse in new gTLDs have been effective.
- 02:00 UTC
- Web conference recording
- Teleconference recording [MP3, 18.2 MB]
- 16:00 UTC
- Web conference recording
- Teleconference recording [MP3, 13.5 MB]
- 02:00 UTC
- Announcement: 19 January 2016 – Join ICANN in a discussion about reviewing New gTLD Program safeguards against DNS abuse
- Background Reading: New gTLD Explanatory Memorandum: Mitigating Malicious Conduct, 3 October 2009